Introduction
Since the beginning of time, humans have used it to protect their possessions from fire and robbery. With the rise of the internet and the IT industry in the twenty-first century, gadgets like smartphones, IoTs, and computers are a part of most people’s everyday lives. Thanks to internet access, people may easily communicate with others, download or upload information, and conduct information searches. Because of this, people depend more on the flow of information. However, online threats like spyware, malware, and viruses could stop this flow of information. Malicious users can take advantage of these vulnerabilities online using free and open-source software.
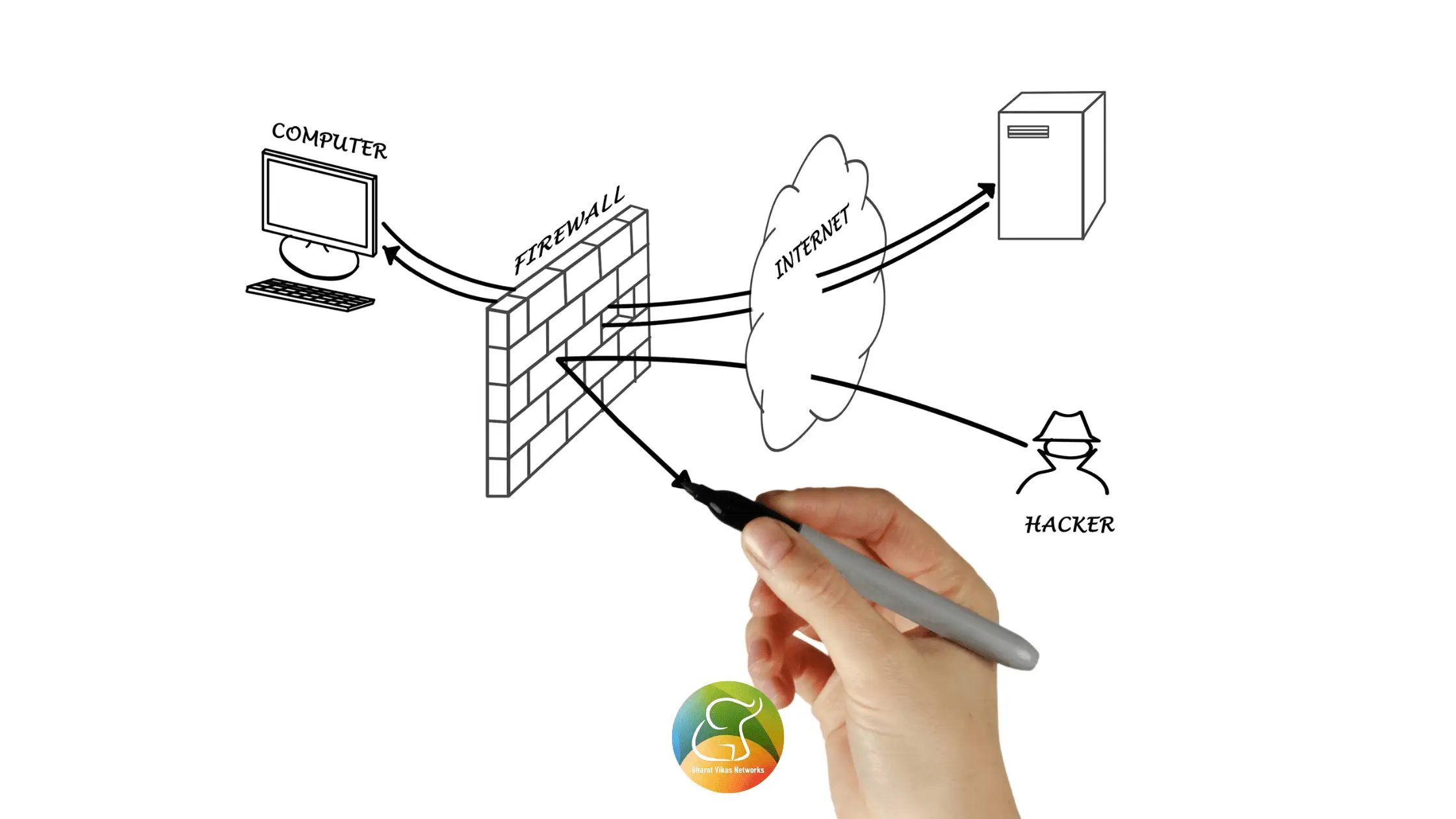
Computer firewalls are now the best way to stop hackers from getting into IT systems and information assets. We will provide you with an overview of Firewalls in computer networking and their types (stateful and proxy).
Firewall Overview
In terms of network security, a firewall can be either a physical computing device or a piece of logical software, or even a combination of both. It works as a porous device that filters out problems in the transmission of packets and information so that they can move through the network within the right limits.
As per generation, firewalls can be divided into different categories. In the first generation of firewalls, a router was used to do stateless packet inspection. There are currently five generations of firewalls, each of which has a unique set of features that improve security and comfort. These generations use a variety of conceptual frameworks and implementation architectures.
The two main security features that a firewall should provide are as follows:
1) Packet filtering: A firewall must be able to decide whether to let digital information packets pass through it or not, based on the security policy or set of rules that are being set up.
2) Application proxy: Firewalls can provide network services to users while protecting their hosts. The firewall is used to stop Internet Protocols from flowing between the secure internal network and the outside network.
Proxy Firewall
Application-level proxy firewalls operate on the OSI model’s top layer. In a transport protocol that is connection-oriented, they serve as agents for breaking connections. One option is to create a proxy firewall between a server and a remote client. The server only knows the identity of the proxy; it is unaware of the user’s identity. Also, the user only knows how to use the proxy; they don’t know who the server is that they are connecting to.
A device that accepts strengthens, and transmits application-level traffic is referred to as an application proxy, sometimes known as an application-level gateway.
Stateful Firewall
Stateful packet inspection or filtering are other names for a stateful firewall. It does a thorough analysis of the connection and payload state between internal and external remote host machines in a network. A stateful firewall is better than a stateless firewall because it uses the state table in its cache to keep track of the status of connections and uses that information to decide whether or not to let traffic through.
A state table in communication keeps track of the hosts’ supplying what data unit when, as well as the state and context of each packet. Stateful firewall filtering may let a previously sent packet through the firewall in exchange for an internal request. In contrast, firewalls for simple packets just consider the packet’s source or destination address when deciding whether to allow or refuse it.
If an incoming packet does not match the state table, the default configuration of an access control list decides whether or not to let it through.
A stateful packet does its job by using TCP and higher layers of the OSI model to limit and control data for the filtering operation. The state table, which is often controlled dynamically, stores connection data.
After the connections have been checked, each one logs into the table. The packet is then sent to its destination based on the ruleset for that connection.
For instance, a firewall may invalidate packets or prevent access to port number 1024+ or any other unsuitable ports for transmission from request servers, whereas the majority of servers respond on normal ports that are in the 0 to 1023 range.
Looking for Firewall solutions? We can help you with that. Contact us at [email protected]
Author

Purushotham
Purushotham is the CTO of BVN Business Solutions. He has 10+ years of experience in the IT industry.