IoT – Internet of things
What is IoT?
The International Telecommunication Union defines IoT as “(an) object of the physical world (physical things) or the information world (virtual world) capable of being identified and integrated into communication networks.”
Quick Fact!
How does IOT work?
Common physical things can communicate virtually with IoT technology, allowing them to be aware of events occurring at a distance or respond to an event that they cannot detect physically. When compared to personal mobile devices, the IoT has limited processing power, storage, and volatile memory. As a result, it may be necessary to link to a Cloud Platform or a Fog Platform for further data processing.
Three major components enable IoT functions:
(i) Hardware—the network of connected, sensor-embedded objects or devices;
(ii) Software—program used for data collection, storage, transporting, processing, and devices instructions;
(iii) Data communication—the protocols and technologies for exchanging data.
What are the Applications of the Internet of Things?
IoT is a part of our daily lives, ranging from basic gadgets like baby monitors, health wristbands, smartwatches, voice-activated speakers, and smart refrigerators to more advanced devices like self-driving vehicles and low-resource devices like wireless body sensor networks (WBAN) and medical wireless sensor networks (MWSN). Simply put, IoT-enabled gadgets are all around us in our homes, businesses, streets, neighbourhoods and cities, and even in our bodies.
wide application of IoT technology
wide application of IoT technology
As much as IoT is crucial in our daily lives, it is certain that IoT will play a crucial role in technological infrastructure in the next year.
IoT devices prediction
IoT devices prediction
While firms race to create new IoT devices with innovative uses, security is often an afterthought in many situations.
What is the architecture of the Internet of Things?
There are currently no recognized standards for IoT network architecture or design. The Internet of Things network may be separated into four major layers based on the flow of data and the various functionalities:
1. Perception/sensing layer-includes perception nodes and networks.
2. Networking/transport layer – has several sub-layers such as access network, core network, and LAN
3. Service/management layer – is where data is processed and analyzed while the application/interface layer is where data is collected.
4. Application/interface layer-Processed information gets consumed and is presented in business applications.
IoT network Layers
IoT network Layers
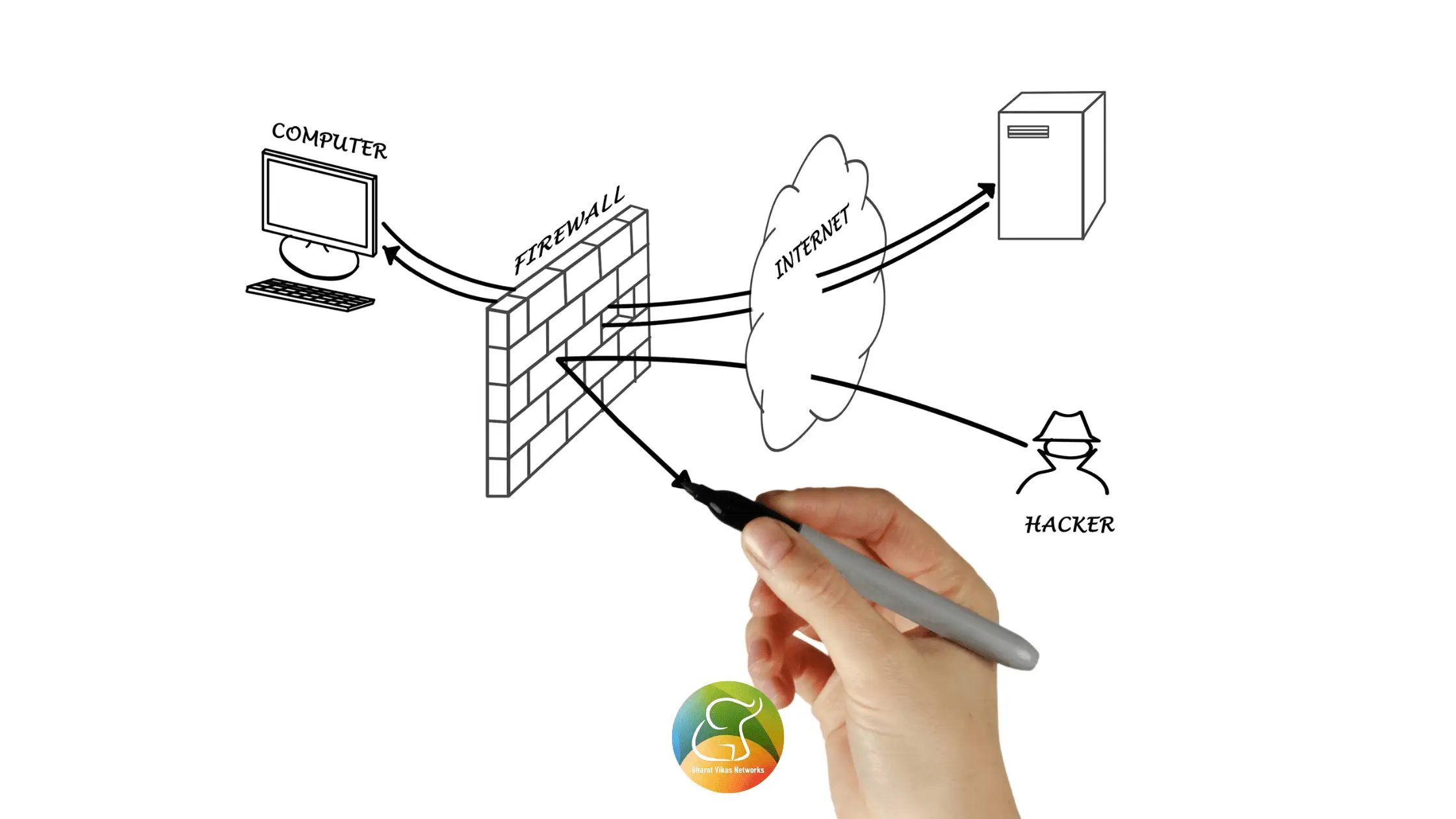
What are the security concerns of the Internet of Things?
Most IoT devices have a basic design that is based on the concept that they can be operated quickly and easily, or that everyday electronics may be converted to IoT by adding Internet connections. “The demands of launching a product rapidly can often lead to the omission of non-visible factors such as security and reliability.” Security problems are obviously not always considered as part of the IoT device production cycle, from hardware/software applications to frameworks.
Security researchers verified that the newest IoT devices communicate via a cloud infrastructure, which has known security flaws and may make IoT devices easy targets. Most IoT devices rely on newly developed, nascent platforms that may have security vulnerabilities. To make matters worse, many IoT devices lack the capability of updating their firmware and software, leaving them incredibly insecure and exposed to future breaches and attacks.
There are two main types of IoT attacks: attacks on architect layers, and attacks on data phases.
Human interactions produce content and data on the traditional Internet. It is common in the area of IoT for smart machines to gather and create data (sensors, actuators). Machines do not lie, but they may be manipulated to send or receive corrupted data.
Top 10 security problems with IoT devices:
1. Weak guessable, or hardcoded passwords;
2. Insecure network services;
3. Insecure ecosystem interfaces;
4. Lack of secure update mechanism;
5. Use of insecure or outdated components;
6. Insufficient privacy protection;
7. Insecure data transfer and storage;
8. Lack of device management;
9. Insecure default settings;
10. Lack of physical hardening.
How to protect our privacy?
We must ensure that the gathered data and data transmission match the requirements listed below:
1) confidentiality—transmitted data, and communication among endpoints, sensors and readers are secured and encrypted;
2) integrity—transmitted data is accurate and complete;
3) authenticity—transmitted data is verified and comes from authorized sensors, endpoints, and readers.
SDN – Software-defined Network
What is Software Defined Networking (SDN)?
SDN is a network architectural method in which programmable switches are placed between the data and control planes to govern and alter data forwarding.
Software-defined networking vs traditional
1) Because traditional networks are hardware-based, their infrastructure necessitates the use of physical devices such as switches and routers, limiting their speed and manipulability. While SDN is software-based, it may be managed virtually via the control plane. Instead of having defined functionalities, SDN can be quickly and readily updated as needed.
2) Traditional network routers need high-level algorithms to identify the destination of packets. When it comes to SDN, the SDN controller communicates with network devices to centrally manage packets based on their configuration.
3) Additionally, the SDN controller provides important debugging tools that the IoT ecosystem may employ to improve security.
What does the IoT with SDN structure look like?
In the IoT with SDN structure, the SDN controller allows up to separate the network into isolated subnets. Furthermore, the SDN Controller communicates with the IoT application using a unique application programming interface (API) known as the ‘Northbound API’. The latter analyses network traffic and take actions depending on the rules that have been specified.
The controller, on the other hand, communicates with network switches using another API (referred to as the “Southbound API”) depending on configured rules. Overall, the combination of IoT with SDN improves IoT operations and security by allowing full and remote control of network setup without requiring direct contact with IoT devices.
SDN and IoT structure
SDN and IoT structure
How does SDN work with IoT?
SDN is implemented via the Openflow Protocol. The SDN switch uses a flow table, which is similar to the routing table used by traditional routers. It does, however, support chaining and allows for the matching of a broader variety of fields, with each flow having its own set of actions.
When a packet arrives at a switch, it is compared to the flow table; if a match is detected, the relevant actions are carried out.
If no match is identified, as is expected with a newly inserted device, the received packet is transferred to the SDN controller through the Southbound API.
The controller then inspects the packet and takes appropriate action. It may create a new flow on the switch to allow subsequent packets to be routed without the involvement of the controller. The SDN application will be notified via the Northbound API.
What is the solution to the Man-in-the-Middle Problem?
Because of the lack of authentication, HTTP is inherently vulnerable to MITM attacks. One of the goals of the SDN – IOT framework is to address this issue. The solution is to utilize HTTP Secure (HTTPS), which adds a transport layer security (TLS) on top of the transport control protocol (TCP) to offer both confidentiality and integrity.
While HTTPS may be able to eliminate the problem, there are two issues to consider before utilizing HTTPS on IoT: code upgrade, and resource constraints.
Using HTTPS instead of HTTP on the IoT will almost certainly necessitate changes to the IoT. To make the modifications, the manufacturer can either provide a software/firmware update over the internet or recall the IoT and manually update it.
Neither of these options is ideal because a device recall will be costly, and updates done over the internet will almost certainly be done via HTTP anyhow, creating an even greater risk since an adversary can possibly gain control of the entire operating system on the IoT with a MITM attack.
However, as compared to devices such as personal computers, IoT devices have higher resource constraints, including processing power, storage, volatile memory, and energy, making it difficult for an IoT device to use HTTPS.
To resolve the problem of code upgrade and resource limits, utilise a TLS/SSL upgrading proxy (referred to as proxy or upgrading proxy) in transparent mode to manage the security layer. To avoid the issue of reconfiguring the IoT device, the resources required for the TLS/SSL channel are offloaded to the proxy device, which operates in transparent mode.
HTTP connections are diverted to the proxy via the switch. This has the extra benefit of simplifying the trusted certificate authority management process, as a proxy is the only device that needs to be aware of the complex public key infrastructure.
What about the traffic separation?
Not all HTTP traffic on the network must be switched to HTTPS. This can be addressed by avoiding unnecessary resource utilization on the proxy when traffic does not need to be upgraded. Other connected devices, such as personal PCs, may not require an HTTPS upgrade because they already use HTTPS. To distinguish IoT traffic from regular network traffic, use the SDN controller to detect IoT traffic by analyzing the source MAC address and SDN switch to redirect IoT traffic to a proxy.
IOT traffic separation
IoT traffic separation
Furthermore, not every IoT traffic must be protected and upgraded to a HTTPS channel. Deep packet inspection (DPI) at the proxy can be used to identify security-related requests (e.g., the SHA-2 hash value of add-on files) and route them through a HTTPS channel. For non-security-related requests, on the other hand, it will function as a normal forwarding proxy.
Separate security related traffic
Separate security-related traffic
SDN in Networking
SDN has the potential to tackle the issue of scalability and the restricted size of ternary content addressable memory (TCAM) better than other systems. Because it is software-based, and with recent hardware developments in terms of processing and memory, SDN is more resilient to limited size concerns and capable of handling the MAC addresses for a large number of IoT devices.
In the future, researchers intend to investigate the usage of a dynamic classification solution and further analyze the system’s scalability.
Looking for computer networking services or IoT services?
Feel free to get in touch with our experts, and get the solution suitable for your requirement.
Author
Purushotham
Purushotham
Purushotham is the CTO of BVN Business Solutions. He has 10+ years of experience in the IT industry.
Latest Post
Securing UniFi Cloud Controller on AWS: A Comprehensive Installation Guide
Securing UniFi Cloud Controller on AWS: A Comprehensive Installation Guide
network as a service
Everything you need to know about NaaS
9 Benefits of Networking as a service (NaaS) for your Firm
SD_WAN
What can SD-WAN(Software Defined-WAN) offer?
SD-WAN
Why SD-WAN? Quick facts on SD-WAN
VPN
Different VPN Solutions: What Do You Need to Know?
BVN logo
Company
About us
Blogs
Contact us
Office
No 47/1, 4th cross LG food road Tavarekere Bengaluru 560029
[email protected]
+(91) 9986861892
Facebook-f
Icon-instagram-1
Twitter
Linkedin
Author

Purushotham
Purushotham is the CTO of BVN Business Solutions. He has 10+ years of experience in the IT industry.