Enterprise Network Security
Enterprise network security for Bharat Vikas Networks focuses on protecting its IT infrastructure through measures like network segmentation, firewalls, VPNs, intrusion detection/prevention systems, endpoint security, and strict access control policies.
Integrated services designed for end-to-end protection and resilience
Intrusion Detection system (IDS) and intrusion protection (IPS)
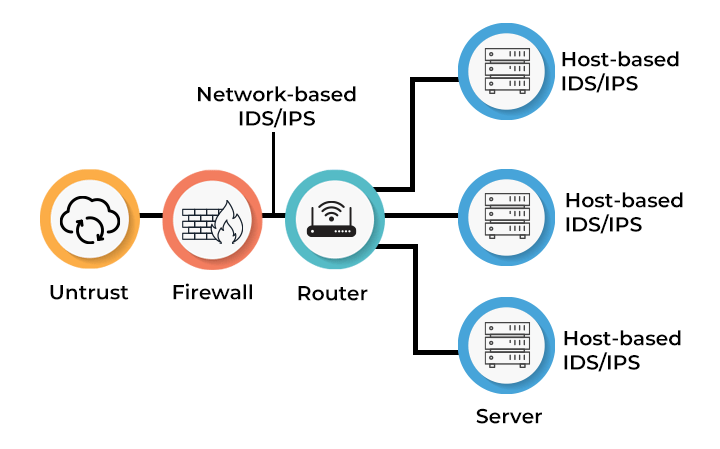
IDS detects and alerts on malicious activities, while IPS detects, blocks, and prevents them in real-time.

Secure Data
Exchange
- Telemetry and Logging: Collecting detailed telemetry data for real-time monitoring and analysis.
- Network Analytics: Using advanced analytics tools to gain insights into network performance and usage patterns.

Firewall
- Telemetry and Logging: Collecting detailed telemetry data for real-time monitoring and analysis.
- Network Analytics: Using advanced analytics tools to gain insights into network performance and usage patterns.

Virtual Private Network (VPN)
Virtual Private Server (VPS)
- Telemetry and Logging: Collecting detailed telemetry data for real-time monitoring and analysis.
- Network Analytics: Using advanced analytics tools to gain insights into network performance and usage patterns.

Authentication
Authorization
Addressing (AAA)
- Telemetry and Logging: Collecting detailed telemetry data for real-time monitoring and analysis.
- Network Analytics: Using advanced analytics tools to gain insights into network performance and usage patterns.

Maintenance, operation and Repair Services
Talk to us 24*/7 for Free consultancy
Our experts can help reduce maintenance cost and minimize downtime. Contact us at: 9986861892

